testsetset
Google today launched the Android Security Rewards program to compensate researchers who find and responsibly disclose vulnerabilities in the company’s mobile operating system. The program currently encompasses the latest available Android versions for Nexus devices available in the U.S. Google Store, which right now means just the Nexus 6 and the Nexus 9.
Android security lead Adrian Ludwig made the announcement at Black Hat’s Mobile Security Summit in London today. Ludwig pointed out that Nexus is the first major line of mobile devices to offer an ongoing vulnerability rewards program.
Eligible bugs include those in Android Open Source Project (AOSP) code, OEM code (libraries and drivers), the kernel, and the TrustZone OS and modules. Vulnerabilities in other non-Android code, such as the code that runs in chipset firmware, may be eligible if they affect Android’s overall security.
Like any bug bounty program, Android Security Rewards includes monetary rewards and public recognition for vulnerabilities disclosed to the Android security team; the reward level is based on the bug severity and on the quality of the report. Only the first report of a specific vulnerability gets rewarded, while bugs initially disclosed publicly or to a third party for purposes other than fixing the bug typically do not.
June 5th: The AI Audit in NYC
Join us next week in NYC to engage with top executive leaders, delving into strategies for auditing AI models to ensure fairness, optimal performance, and ethical compliance across diverse organizations. Secure your attendance for this exclusive invite-only event.
Google promises to pay for reproduction code, patches, and tests for vulnerabilities affecting Nexus phones and tablets (we’re of course expecting new Nexus devices to debut with Android M next quarter). Other Google devices (the company specifically named the Nexus Player, Android Wear, and Project Tango) are not eligible for Android Security Rewards. The company’s message was clear, though: If all goes well with Nexus, the program may expand beyond that brand.
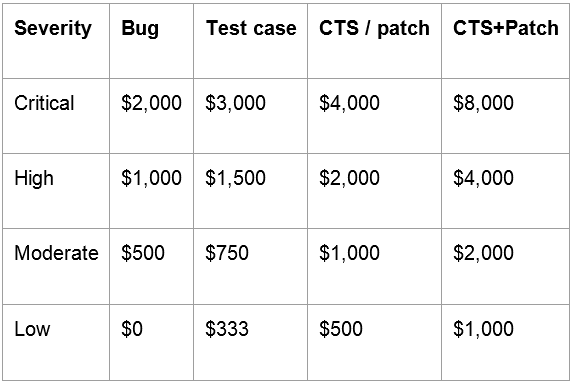
Larger rewards are given to security researchers who invest in tests and patches that work around Android’s platform security features like ASLR, NX, and sandboxing. Google’s base rewards are $2,000 for critical, $1,000 for high, and $500 for moderate severity vulnerabilities. The company will “consider” offering rewards for test cases and patches for low-severity vulnerabilities.
Up to 1.5 times the base amount will be rewarded if the bug report includes standalone reproduction code or a standalone test case, and up to 2 times will be rewarded if the bug report includes a patch that fixes the issue or a CTS test that detects it. If both are provided, there’s a potential 4-times reward modifier.
The following table sums up the typical rewards:
There are also extra rewards for functional exploits:
- An exploit or chain of exploits leading to kernel compromise from an installed app or with physical access to the device will get up to an additional $10,000. Going through a remote or proximal attack vector can get up to an additional $20,000.
- An exploit or chain of exploits leading to TEE (TrustZone) or Verified Boot compromise from an installed app or with physical access to the device will get up to an additional $20,000. Going through a remote or proximal attack vector can get up to an additional $30,000.
In the end, the final amount is up to the Android security team: “We may decide to pay higher rewards for unusually clever or severe vulnerabilities; decide that a single report actually constitutes multiple bugs; or that multiple reports are so closely related that they only warrant a single reward.” And of course, the above bugs can’t already be covered by Google’s other reward programs.
Since 2010, Google has paid security researchers over $4 million in rewards across its bug bounty programs. The company is also spending more and more every year: It doled out $1.5 million to over 200 security researchers last year alone.
The Android Security Rewards program is in addition, and as a complement, to Google’s existing security programs. Android will continue to participate in Google’s Patch Rewards Program, which pays for contributions that improve the security of various open-source projects.
“As we have often said, open security research is a key strength of the Android platform,” Google declared. “The more security research there is focused on Android — the stronger it will become.” In other words, Google still believes bug bounties are well worth the expense.
Oh, and if you’re a security researcher who isn’t interested in money, the company will offer to donate double the amount of your reward to an established charity. After 12 months, unclaimed rewards will be donated to a charity of Google’s choosing.