testsetset
Google released its Android Security 2017 Year in Review report today, the fourth installment of the company’s attempt to educate the public about Android’s various layers of security and its failings. One of the most interesting learnings to come out of the report is that 60.3 percent of Potentially Harmful Apps (PHAs) were detected via machine learning.
The detection is done by a service called Google Play Protect, which is enabled on over 2 billion devices (running Android 4.3 and up) to constantly scan Android apps for malicious activity. Play Protect uses a variety of tactics to keep users and their data safe, but machine learning is particularly effective in helping catch PHAs.
Automatic and manual scanning
When Google shared earlier this year that more than 700,000 apps were removed from Google Play in 2017 for violating the app store’s policies (a 70 percent year-over-year increase), the company credited its implementation of machine learning models and techniques to detect abusive app content and behaviors such as impersonation, inappropriate content, or malware.
But the company did not share any details. Now we’re learning that 6 out of every 10 detections were thanks to machine learning. Oh, and the team says “we expect this to increase in the future.”
June 5th: The AI Audit in NYC
Join us next week in NYC to engage with top executive leaders, delving into strategies for auditing AI models to ensure fairness, optimal performance, and ethical compliance across diverse organizations. Secure your attendance for this exclusive invite-only event.
Every day, Play Protect automatically reviews more than 50 billion apps — these automatic reviews led to the removal of nearly 39 million PHAs last year, Google shared. Play Protect automatically checks Android devices for PHAs at least once every day, but users can conduct a review manually if they want:

Until only recently, Play Protect required devices to be online. When Google found that nearly 35 percent of new PHA installations were occurring while a device was offline or had lost network connectivity, it moved to develop a new feature to address the problem. In October 2017, Play Protect got an offline scanning feature, which has since prevented 10 million more PHA installs.
Google Play versus third-party app stores
Android devices ship with the Google Play store, which in most countries is where users get their apps. In some countries, however, third-party Android app stores are the only option or a popular alternative, or users share apps directly between themselves. Google revealed in its report that Android devices that only download apps from Google Play are 9 times less likely to get a PHA than devices that download apps from other sources, as you can see below.
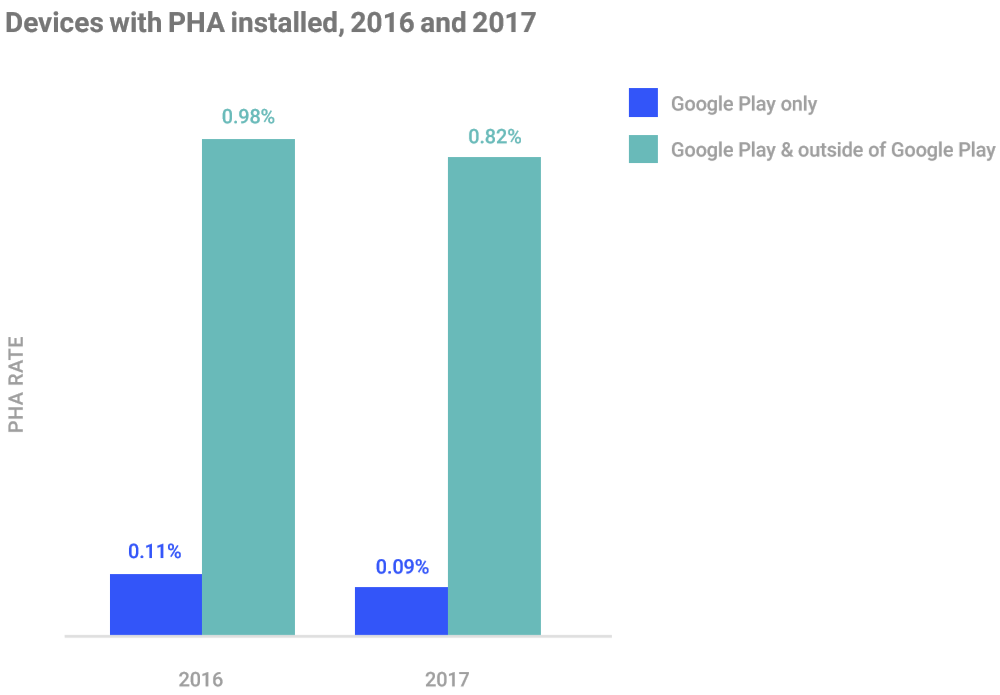
In 2017, 0.56 percent of all Android devices scanned by Play Protect had installed a PHA, compared to 0.77 percent in 2016. Furthermore, the annual probability that a user downloaded a PHA from Google Play was 0.02 percent in 2017, down from 0.04 percent in 2017.
But the real progress was made with Google’s desire to protect Android users regardless of where they got their apps. Play Protect can remove any PHA from the Google Play store, but of course it can’t do the same for third-party app stores. Play Protect can only warn an Android user that an app is a PHA, although in the case of ransomware or banking phishing apps, it can also block the installation. Google thus tracks installation attempts for apps installed from outside of Google Play to see if Play Protect is having an impact.
Play Protect prevented 74 percent of PHA installation attempts with warnings and protections in 2017, compared to 55 percent in 2016. Google did not break out the remaining 26 percent between PHAs that were installed before Google identified them as threats and users who decided to ignore Play Protect’s warnings to install the PHA. Still, 1.22 percent of all app install attempts from outside of Google Play ended with a PHA installation in 2017, compared to 3.32 percent in 2016.

Given that Play Protect doesn’t just secure Google Play, it seems like a more apt name would be Android Protect. The report also talked about rewards given out by Android’s bug bounty programs, though the high-level results were already shared earlier this year.

