North Korea’s cyberattacks have been well documented over the years. But a collaboration between McAfee and Intezer security researchers has shown previously undiscovered links among the various North Korean malware families and some of the most successful cyberattacks to date.
Jay Rosenberg of Intezer and Christiaan Beek of McAfee are talking about their discovery at the Black Hat 2018 security conference in Las Vegas this week. They say they found links by examining the reuse of code among malware and their malware attack campaigns.
For example, four examples of reused code in larger-scale nationalism-motivated campaigns were discovered to only be seen in malware attributed to North Korea.
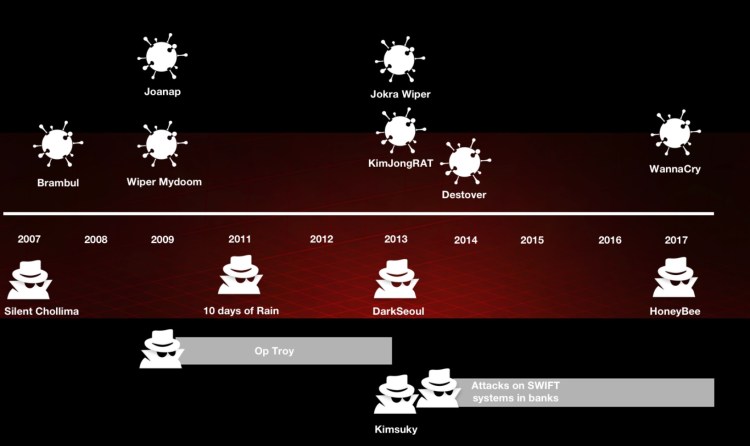
The research also details the different tools believed to be used by specific teams of North Korea’s cyber army, and provides a distinct timeline of the evolution of attacks that began when North Korea entered the stage as a significant threat actor.
June 5th: The AI Audit in NYC
Join us next week in NYC to engage with top executive leaders, delving into strategies for auditing AI models to ensure fairness, optimal performance, and ethical compliance across diverse organizations. Secure your attendance for this exclusive invite-only event.
Attacks from the online groups Lazarus, Silent Chollima, Group 123, Hidden Cobra, DarkSeoul, Blockbuster, Operation Troy, and Ten Days of Rain are believed to have come from North Korea. The security researchers wanted to know what a distributed denial of service (DDoS) and disk-wiping attack from July 4, 2009 has to do with WannaCry, one of the largest cyberattacks in history.
“Bad actors have a tendency to unwittingly leave fingerprints on their attacks, allowing researchers to connect the dots between them,” the security researchers wrote in a post. “North Korean actors have left many of these clues in their wake and throughout the evolution of their malware arsenal.”
The post represents months of research involving code analysis that shows similarities between samples attributed to the Democratic People’s Republic of Korea.
North Korea wants to be as self-sufficient and independent as possible. However, when it comes to acquiring products such as oil, food, and foreign currency for trading, the country lacks resources and has to find ways of acquiring them. To do that, it has turned to enterprises dealing in gambling and illegal drugs.
In 2005, the United States investigated a couple of banks in Asia that seemed to have ties with North Korea and be operating as money laundering sites. One bank, in particular, is controlled by a billionaire gambling mogul who started a casino in Pyongyang and has close ties to Pyongyang. That bank, based in Macau, came back into the picture during an attack on the SWIFT financial system of a bank in Vietnam in 2015. The Macau bank was listed twice in the malware’s code as a recipient of stolen funds.
“By identifying reused code, we gain valuable insights about the ‘ancestral relations’ to known threat actors or other campaigns,” the report said. “In our years of investigating cyber threats, we have seen the DPRK conduct multiple cyber campaigns. In North Korea, hackers’ skills determine which cyber units they work for. We are aware of two major focuses of DPRK campaigns: one to raise money and one to pursue nationalist aims.”
North Korea’s Unit 180 is responsible for illegally gaining foreign currency using hacking techniques. The second workforce, Unit 121, operates larger campaigns motivated by nationalism, gathering intelligence from other nations and in some cases disrupting rival states and military targets.
The security researchers created a timeline of the malware samples associated with North Korea. To understand the similarities between the campaigns, they used Intezer’s code similarity detection engine to plot the links between a vast number of these malware families.
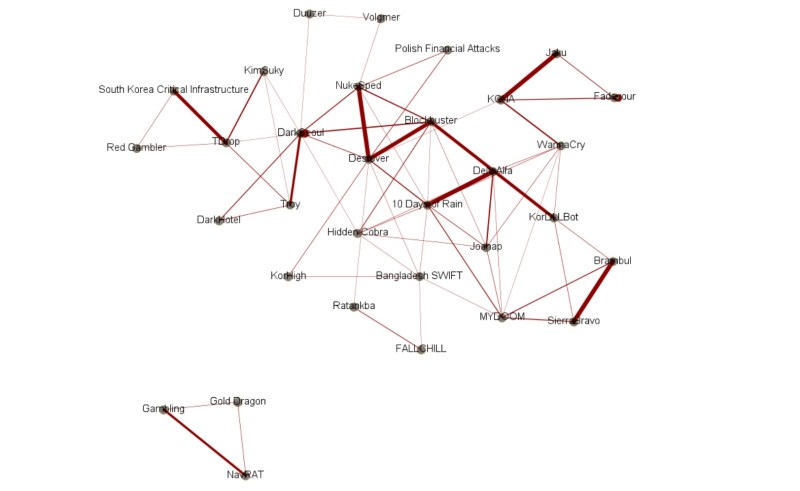
Above: Darker lines show deeper code connections between various malware families.
In the graph above, a thicker line correlates to a stronger similarity. In defining similarities, the researchers took into account only unique code connections, and disregarded common code or libraries.
“We can easily see a significant amount of code similarities between almost every one of the attacks associated with North Korea,” the researchers found. “Our research included thousands of samples, mostly unclassified or uncategorized.”
By applying what they learned from comparisons and code-block identifications, the researchers uncovered possible new links between malware families and the groups using them.
The malware attributed to the group Lazarus has code connections that link many of the malware families spotted over the years. Lazarus is a collective name for many DPRK cyber operations, and the researchers clearly saw links between malware families used in different campaigns.
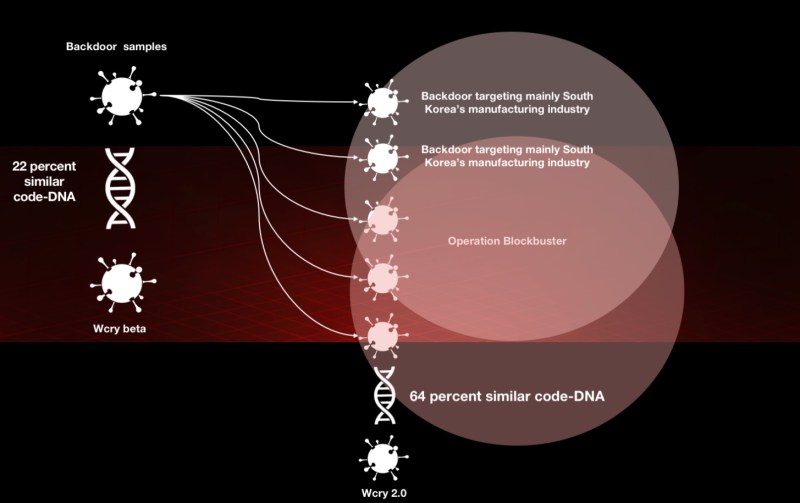
Above: The shared DNA among North Korean malware attacks.
In 2018, the researchers saw examples of campaigns in which attackers used PowerShell to download and execute these droppers.
The researchers hope their work will help the security community organize the current mess related to North Korean malware and attack campaigns. The authors credited Costin Raiu for providing them with samples they did not have in their collections.