testsetset
At Google Cloud Next 2019 today, Google announced phones running Android 7.0 Nougat and higher can now double as a Fast Identity Online (FIDO) security key. You can thus use your Android phone to protect your personal Google account, and your G Suite, Cloud Identity, and Google Cloud Platform work accounts. (Android tablets aren’t supported — Google specifically limited the functionality since users are more likely to have phones with them.)
This means Android phones can move from two-step verification (2SV) to two-factor authentication (2FA). 2SV is a method of confirming a user’s identity using something they know (password) and a second thing they know (a code sent via text message). 2FA is a method of confirming a user’s identity by using a combination of two different factors: something they know (password), something they have (security key), or something they are (fingerprint).
Why security keys are superior
Using 2FA means a remote hacker can’t use phishing to trick you into handing over your online credentials. 2SV — entering a code sent via a text, mobile app, or push notification — is better than just using a password. But 2FA via a security key or phone is even better.
“It’s a second thing that I carry around with me wherever I want to login somewhere and I need to prove my identity by having this thing in my hand,” Google product manager Christiaan Brand explains. “But it’s doing something for us. It’s proving that I’m at the correct website at the point in time when I am trying to login. So the solution here really is that security keys prevent you from sending your credentials to a phishing website.”
June 5th: The AI Audit in NYC
Join us next week in NYC to engage with top executive leaders, delving into strategies for auditing AI models to ensure fairness, optimal performance, and ethical compliance across diverse organizations. Secure your attendance for this exclusive invite-only event.
“You’re trying to sign in, you’re on a site that looks exactly like the real Google; however, your login will not succeed if you use the security key, because the security key will block it as you’re on an incorrect website,” Brand continues. “All other forms of 2SV have levels of assurance that the fundamental problem with them are that you can still fall victim to phishing. You can still be tricked into entering all of your credentials, be it your username, your password, and your one-time password, even approve a mobile login using Postgres technology, because there is no way that your browser on your local machine knows that you’re being duped into revealing your credentials to an incorrect website.”
FIDO security keys prevent your account from being phished by requiring you to plug in and tap your physical device. Google wants to bring those benefits to more people by having Android phones act as security keys.
How Android phone security keys work
Unlike other similar technologies, Google’s solution has a local requirement. “The big difference here is that local proximity,” Brand emphasized. “The fact that your browser on your machine and your phone communicate using a local protocol and does not go via the cloud. All other push-based technology so far is kind of based on the fact that there’s a message being sent throughout the cloud. Here, we’re saying no, the message will be local. And that is essential to this phishing resistance. Having this local protocol between the two devices is what makes this technology strongly resistant to phishing.”

FIDO’s proximity requirement ensures that the user trying to login and the security key are in the same location. With security keys, that is accomplished via the USB port or via Bluetooth. With Android phone security keys, Google chose Bluetooth for convenience purposes.
“Asking the user to have a cable ready that’ll fit both their device and the machine they’re trying to sign in at some point in time almost takes away all the convenience of being able to use your phone,” Brand noted. “The chance that you have your phone there is very, very high. But the chance that you have the exact correct cable is very low. At that point in time, it might just be the same as having to carry around a physical security key.”
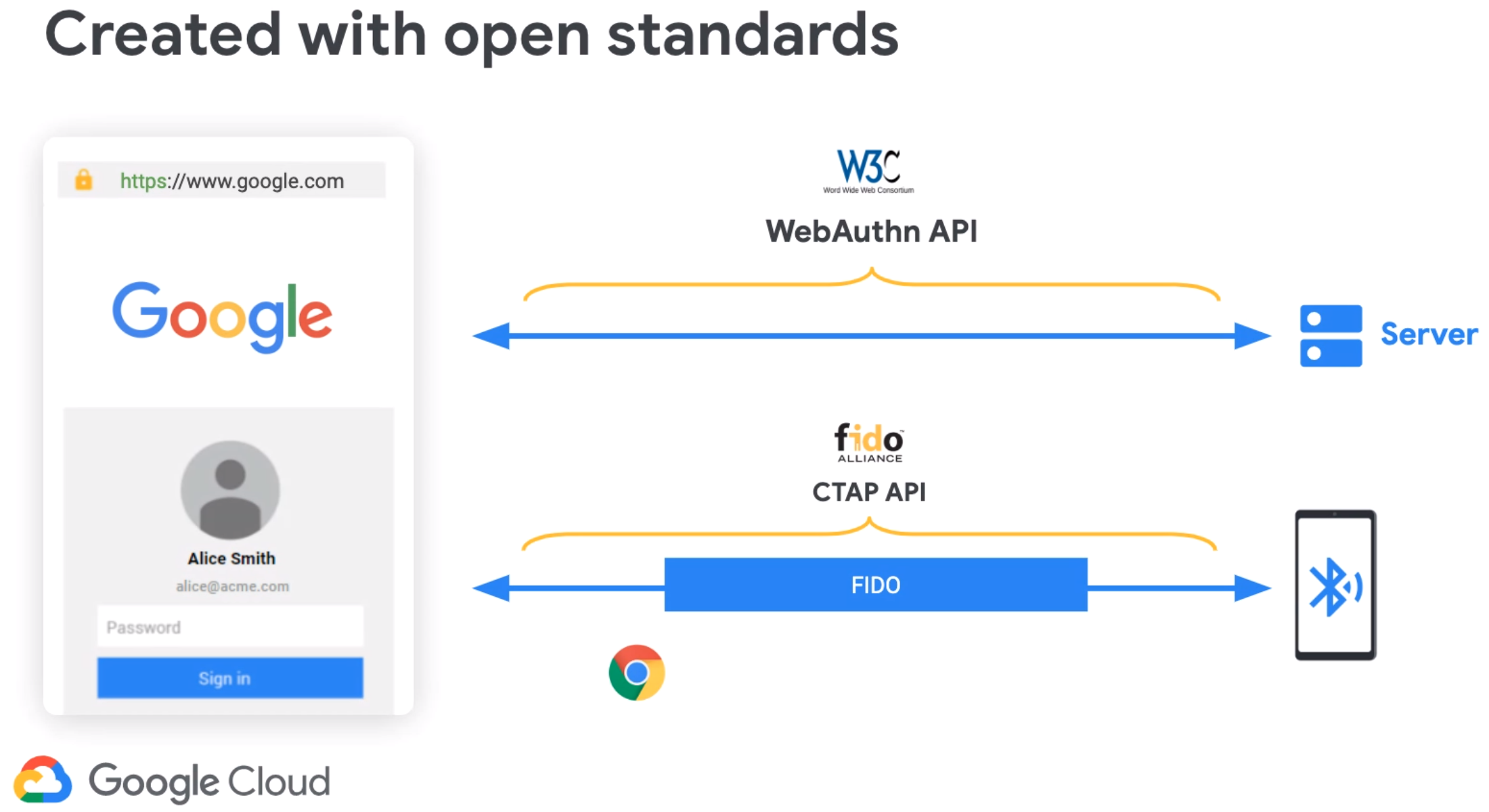
Google’s solution uses the FIDO protocol between your computer and phone (CTAP API), and also requires that the browser tells the phone which website the user is viewing (WebAuthn). The company further used the available extension mechanism to build a local proximity protocol on top of Bluetooth. Called cloud-assisted Bluetooth Low Energy (caBLE), the extension doesn’t require pairing, installing an app, or plugging anything in.
Using your Android phone as a security key
To use your Android phone as a security key, you will need a Bluetooth-enabled Chrome OS, macOS X, or Windows 10 computer with Chrome 72 or higher. Follow these steps to get started:
- Sign into your Google Account on your Android phone and turn on Bluetooth
- On your computer, navigate to myaccount.google.com/security (you have to be signed into the same account)
- Select 2-Step Verification
- Click “Add a security key”
- Choose your phone from the list of available devices
Everyone will have to go through this process before they can use their Android phone as a security key. (Google plans to run a promotion encouraging Google account users to enable the feature if their phones are eligible to use as a security key.)

Once enabled, the user experience is straightforward. After you type in your password, your phone will prompt you to approve the login. You’ll just have to hit a button on your screen. On Pixel 3 devices, you’ll have to hit the volume-down button, which is hardwired to the Titan M chip — where Google stores your FIDO credentials for that extra bit of assurance.
![]()
“Note that the user experience when using your phone as your security key is very simple. It is more or less the same as approving a prompt on your phone, which is a big plus,” Brand told VentureBeat. “Under the covers, however, the phone and computer are communicating with the FIDO CTAP protocol over Bluetooth and the website and computer are communicating with the WebAuthn protocol and this adds the phishing-resistance. This is the crucial and huge additional security boost.”
Limitations
At Google Cloud Next 2018, Google launched the $50 Titan Security Key, its own take on a FIDO security key. Maybe it’s fitting that Google Cloud Next 2019 makes that security key less useful.
We say less useful because Google still recommends that you use your phone as an additional security key. If you lose your phone, it’s good to have a backup USB key at home, especially if you’re a consumer. An administrator can always reset your work account. If you’re a consumer, however, and you lose your security key, you’re out of luck.
The phone security key solution isn’t limited to any specific geographies because it’s being rolled out via Google Play Services, which is how the company can offer it on older Android devices. It requires Chrome, but because Google built it using open standards, the company hopes other browsers will adopt it as well. The same goes for iOS: Google hopes the functionality will work on Apple’s mobile devices one day too.
But for now at least, the feature can only be used for 2FA on Google accounts. Google has submitted caBLE to FIDO and it’s under review by the working group. Letting other companies use the technology is on the roadmap, but Google wouldn’t commit to a date.