Presented by Intel
Malicious attackers are increasingly burrowing lower in the computing stack, below the operating system. A growing wave of threats seeks to modify or inject malware into the system’s BIOS/ UEFI firmware in hopes of stealing information, identities, and privileges. Where you see people booting laptops at a coffee shop, a firmware attacker sees open basement windows and a data ATM.
What makes firmware implants so potentially dangerous – and appealing to bad actors ? How do enterprises and industry vendors reduce risk from this complex new attack surface and environment?
Rising threat ducks traditional defenses
Over the last three years, the number of firmware vulnerabilities has grown nearly five-fold, according to the NIST National Vulnerability Database. Mobile and remote workers on public networks may be especially exposed; same with those using non-company devices.
Unfortunately, these firmware exploits can be undetectable by traditional antivirus programs, security practices, and threat systems models. To defend against the deep risk, businesses of all sizes need to make protection of endpoint PC hardware and firmware a top-of-mind priority, alongside network and software security.
Effective protection requires coordinating multiple hardware, software, firmware products, protections, and vendors. A holistic approach is key, with hardware playing a key role. Says Michela Menting, Director, ABI Research: “While it can be implemented in software, it is only through dedicated hardware that the root of trust is truly immutable.”
The stakes are high: Much critical corporate data resides on unprotected desktops and laptops; some 61% of data breaches involve stolen credentials or phishing.
Foundation: A firm understanding of the foe
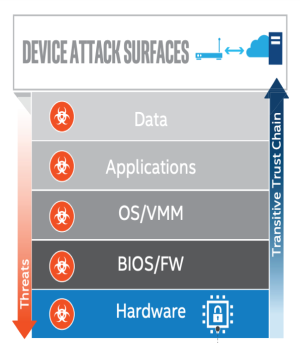
Firmware hacks compromise a PC or device before it starts. They do so by injecting malicious software into the low-level code that governs hardware prior to system boot and during runtime. Once in place, the rogue code can modify and subvert the firmware, target OS components, access high-level software, and much more. Basic Input Output System (BIOS) and newer Unified Extensible Firmware Interface (UEFI) are targets.
Source: Intel
Firmware hacks can take multiple paths into your devices and organization. Malware, rootkits, and bootkits are popular delivery mechanisms. Infected USBs and devices are another; so are infected drivers and bad firmware from a legitimate device maker. But physical access is not required: malicious code can be delivered remotely via Wi-Fi, Ethernet, Bluetooth – any kind of network connectivity, including merely checking for a newer version of firmware.
The attacks can be dangerous for several reasons. Because they do their dirty work deep in a system’s cellar, firmware hacks are hard to find. They’re often persistent; once in place, they enable ongoing harm. They’re sneaky, able to piggyback onto, infect, or replace legitimate firmware updates needed, for example, to fix bugs. And they’re resilient, resisting reinstallation of the OS and even hard drives.
But perhaps most ominous is their ability to access, spy on, steal, alter, and destroy individual and enterprise data – the coin of the modern realm – undetected. Here’s how and why: Hardware components are accessed by firmware, itself used by the OS to store critical secrets and data: Windows Authentication, single-sign-on tokens, Windows Hello, your fingerprint, the virtual Trusted Platform Module, to name a few. Anyone accessing these things can basically be you. That means they can do some pretty damaging things, not only to your end user data, but to the corporate resources you access with these things.
Why action now is crucial
Several broader trends and developments amplify the importance and urgency of better managing the expanding array of firmware exploits and attacks.
Sophisticated new variations. Firmware attacks are not new. Less known than ransomware, worms, botnets, and Trojans, they’ve been around since the mid-1980s. What’s changed is their easy availability, sophistication, and variety.
Last fall, for example, security researchers made an alarming discovery: Lojack anti-theft software had been weaponized by a notorious Russian cyber espionage group known (among other aliases) as Fancy Bear. The “trojanized” version, renamed LoJax, implemented in firmware (UEFI/BIOS), injected itself into the startup routine of affected devices. There, a module mimicked legitimate firmware, resisting OS re-installation or hard drive replacement while it bricked systems, stole data, or granted unauthorized access. It was the first UEFI rootkit found “in the wild,” and a good example of clever, diabolical mutation. Security experts called the incident a wake-up call for organizations and industry vendors worldwide.
Widening adoption. Firmware exploits have become a growing part of the modern hacker arsenal – and not just for governments. “Attack trends and malware almost always eventually trend down-market, from state operators to organized crime to less sophisticated criminal groups to script kiddies,” notes firmware and hardware security researcher Eclypsium. “What was originally part of an APT (Advanced Persistent Threat) campaign becomes commonplace within months and years.” As cyberattacks continue to grow more sophisticated, methods that were once difficult become more streamlined and available.
More mobile workers. Today, more people work outside of offices and log on remotely. In fact, 70% of people globally work offsite at least once a week. Regular work at home has grown by 159% since 2005, more than 11x faster than the rest of the workforce and nearly 50x faster than the self-employed.
These shifts put a growing population outside of on-premise firewalls and other protections. Unfortunately, many IT departments still have limited ways to assess and secure networks and devices they don’t own. That makes PCs with higher levels of security assurance essential for safeguarding end user data and corporate resources, in office or out.
Increasing damage. Average cost of a data breach for a U.S. company has risen to $8.19 million. The figure includes direct and indirect expenses related to time and effort, customer churn as result of bad publicity, and regulatory fines.
Poor preparedness. Firmware security is widely overlooked. ISACA found widespread lack of planning and preparedness, with only 8% of respondents saying their organizations were ready for firmware vulnerabilities and exploits. Typically, visibility is limited, patching slow and manual, and prevention non-existent. Response is hardly better: 77% of global businesses surveyed by the Ponemon Institute lacked a consistently applied cybersecurity incident response plan.
New threats demand new protections
Clearly, firmware attacks pose a complicated and growing challenge. Right now, the legacy model of software protecting software simply may not keep up with advancing threats against digital security, safety, and privacy. The traditional solution of last resort – ripping out and replacing the entire motherboard – is hardly optimal

Image credit: Intel
Primary industry vendors and government are taking a lead role in combatting hardware-based attacks. Notable initiatives and groups include the Unified Extensible Firmware Interface Forum, Project Zero, CERT, the Cybersecurity and Infrastructure Security Agency (CISA), and Open SSH Project, among others.
At the industry level, broad ecosystem cooperation has produced innovative new security technologies that go beyond software and human-based approaches.
A leading example is Intel Hardware Shield. Available only on the Intel vPro platform, it is a collection of technologies anchored in hardware. The solution works on several levels to help reduce platform attack surfaces.
First, BIOS/UEFI firmware is hardened by locking down and managing memory usage. Essentially, the system boots on bare metal, in a locked room. Doing so helps reduce the risk that modified or new malicious code could be injected in the Systems Management Module (SMM). Second, it helps harden the OS by reducing the risk that a vulnerability in BIOS/UEFI firmware could be used by malware to launch an attack on the OS. Third, it facilitates a more trustworthy and attestable assessment of the platform state at runtime via optional hardware-to-software reporting capability.
On the OS side, Microsoft announced Secured-core PCs that meet device requirements to isolate firmware and operating system to prevent, rather than detect, OS attacks. Secured-core PCs support System Guard Secure Launch, which uses the Dynamic Root of Trust Measurements, and meets additional Windows requirements for devices.
Similarly, on the device side, OEMs are also taking major steps to better protect users, with solutions such as Dell SafeBIOS, HP Sure Start, and Lenovo Think Shield. Intel Hardware Shield works with OEM solutions to help protect the BIOS and lock down sensitive information.
Ecosystem and enterprises: Steps to safety
For their part, other OEMs, OSVs, systems integrators, enterprises, and other industry players also should take measures to protect their customers and employees.
Keep all software up to date. Software is constantly changing; the industry regularly finds new security issues. It’s basic but crucial to keep current on updates for operating systems, kernels, third-party libraries (both open and closed source), as well as software for virtual machines and containers.
Adopt best practices for development and operations. These include using well-maintained and reputable libraries, carefully evaluating open source packages, and designing architecture to separate secret data and user data. Many of these also help protect against side-channel attacks.
Assess risk. Basic analysis can help you understand the potential exposure of sensitive data to firmware-based attacks.
Attacking the root of the problem
Just as spraying exposed leaves doesn’t protect roots, safeguarding hardware and firmware foundations requires deep treatment. End users require high-performing, responsive devices that can evaluate and maintain the integrity of software, firmware, and hardware.
While PCs may represent a smaller investment compared to back-end infrastructure, they are crucial to security. Hardware-based security — features built-in to the hardware — provides an important layer of protection for business devices, identities, applications, and data. Forward-looking buyers and sellers will remain committed to staying ahead of dangerous and deep firmware cyber-threats.
Sponsored articles are content produced by a company that is either paying for the post or has a business relationship with VentureBeat, and they’re always clearly marked. Content produced by our editorial team is never influenced by advertisers or sponsors in any way. For more information, contact sales@venturebeat.com.