testsetset
Endpoint verification — a Google Cloud tool that enables network managers to see screen lock, disk encryption, OS version, and other data about devices accessing corporate information — is becoming a bit more versatile starting today. Now admins can designate endpoint machines running Chrome as “approved” or “blocked,” and use those tags to configure access levels within Access Context Manager. Moreover, they can decide whether additional review is needed for newly registered devices before they’re tagged as approved.
In a blog post, Google notes that it is bringing desktop access controls in line with what’s available for mobile devices through Google Cloud’s mobile device management suite.
Here’s what’s new, specifically: Those with the right credentials can view the entire inventory of PCs accessing sensitive data and approve or block access for specific devices based on “any criteria” — for example, lost laptops, or PCs belonging to newly promoted users who need access to an expanded set of internal apps.
June 5th: The AI Audit in NYC
Join us next week in NYC to engage with top executive leaders, delving into strategies for auditing AI models to ensure fairness, optimal performance, and ethical compliance across diverse organizations. Secure your attendance for this exclusive invite-only event.
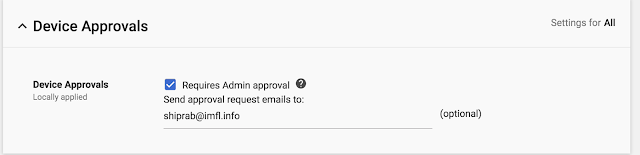
To get started, you first need to register devices with endpoint encryption by turning on endpoint sync in the Admin Console and installing the endpoint verification extension (in Chrome browser and Chrome OS) or native helper (on Mac and Windows devices). Once that’s done, head to Admin Console > Device Management > Setup > Device Approvals, which is where you’ll see a checkbox to set an access policy (by default, devices will be approved and can be later blocked) along with a field for the email that’ll receive approval request notifications.

After a device has been registered via endpoint verification, you’ll be able to switch on access restriction in the Access Context Manager. To approve or remove access, launch Admin console > Device Management > Device Approvals, which will pull up a list of clients in a pending approval state.
All future “approve” and “block” actions will be logged as audit events in the Admin Console for posterity, Google says, and further access policies can be configured in Access Context Manager.

