Watch all the Transform 2020 sessions on-demand here.
Containers — sets of self-contained executables, binary code, libraries, and configuration files — are ubiquitous in cloud computing. According to a survey by managed service provider Diamanti, cloud-native apps were the No. 1 container use case for 33% of organizations in 2019. That’s surely music to the ears of Santa Barbara, California-based Anchore, which Saïd Ziouani and Daniel Nurmi cofounded in 2016 to help organizations implement secure container-based workflows. The company today announced the close of a $20 million in series A financing led by SignalFire, bringing its total raised to around $30 million.
“We created Anchore to empower developers to build secure software quickly and more efficiently,” said Anchore CEO Ziouani, who said the fresh capital will be put toward R&D. “Given our progress to date backed by the strong adoption this past year, we’re now ready to scale our sales, professional services, and engineering resources globally to meet the need and achieve our mission to bring the benefits of container workflow security to customers around the world.”
Anchore offers container inspection and compliance solutions tailored for a range of different applications, including open source projects and large teams in highly regulated industries. They’re built atop the Anchore Engine, a tool for deep image inspection and vulnerability scanning that can be used to generate reports and define continuous integration/deployment pipeline policies, and that searches for attack vectors in apps and operating system (OS) packages while ensuring secrets like passwords, API keys, and other sensitive information aren’t exposed.
Anchore’s products are able to identify non-OS third-party libraries, like Java archives and Node.js NPMs, and they support both the whitelisting and blacklisting of elements like usernames, user IDs, licenses, packages, and images in their entirety. Plus, they can suss out configuration files, file permissions, unpackaged files, and anything else that requires uncovering, and they can perform checks on the contents of Dockerfiles and Docker histories for any container image.
June 5th: The AI Audit in NYC
Join us next week in NYC to engage with top executive leaders, delving into strategies for auditing AI models to ensure fairness, optimal performance, and ethical compliance across diverse organizations. Secure your attendance for this exclusive invite-only event.
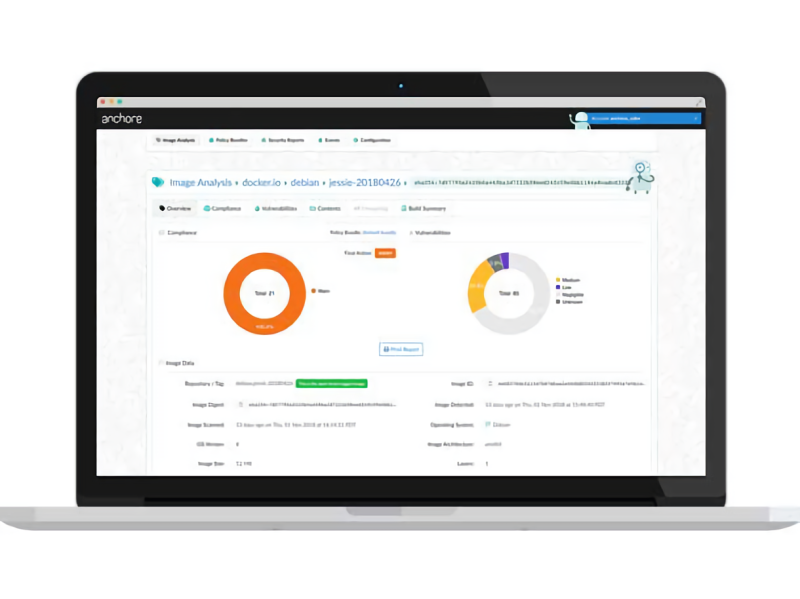
Anchore’s offerings integrate with container registries to scan their contents and ensure images comply with existing policies. They automatically fetch the latest available data and scan images from the registries specified, making available reports and evaluation results through command-line and web interfaces. And they support the use of webhooks to trigger action in other systems — including cloud-hosted or on-premises Kubernetes environments and continuous integration/deployment systems like CloudBees, GitHub, GitLab, CircleCI, and Codefresh — when problems are discovered.
Anchore Enterprise enables users to view and browse repositories, create and define policies, and generate reports on the fly. It boasts a roles-based control system that allows admins to grant access to scanning and policy operations, as well as an on-premises feed that maintains up-to-date vulnerability data without requiring an active internet connection. A built-in policy editor lets clients define policies using visual tools, while a compliance dashboard helps to summarize compliance status and drill down for actionable results.
As for Anchore Federal, it’s targeted at federal agencies with policies designed to meet National Institute of Standards and Technology (NIST) standards and comply with Department of Defense container-handling requirements. Like Anchore Enterprise, it’s agentless, supporting deployments in a number of environments. And it’s plug-and-play with Jenkins, CircleCI, and custom pipelines.
The container security market is anticipated to be worth $2.178 billion by 2024, and Anchore by all appearances is making short work of it. Despite competition from Lacework, Sysdig, Aqua Security, and others, it’s nabbed big clients including Cisco, eBay, Atlassian, Nvidia, and Red Hat, and the United States Department of Defense made it a required component of the agency’s DevSecOps Reference Architecture.


