The current cycle of investment in cybersecurity began in 2012, catalyzed by three major IPOs: Proofpoint, Splunk, and Palo Alto Networks. As is typical, big exits in a space significantly increase investor confidence and drive up supply of capital as additional investors rush in hoping to find the “next big thing.”
2013 saw another major exit with the “eye-popping” IPO of FireEye. It also became the year that cybersecurity rocketed to the forefront of public attention — first after the Edward Snowden incident and again after major breaches at Adobe Systems, the Target Corporation, and Heartland Payment Systems, each of which exposed more than 100 million records. Security has always been a game of cat and mouse, but these events demonstrated how fat the cat had become.
Entrepreneurs and investors took note of two challenges in particular:
- Many companies weren’t even doing the basics right. Existing products were either never fully deployed or not used effectively, and best practices were falling by the wayside. This was usually the result of understaffed security teams being overwhelmed with alerts, many of which were false positives. Security products were also known for impeding productivity, so business users would find ways to get around them, exposing an enterprise to a potential breach.
- The previous generation of security products were just plain inadequate. Not only had the bad guys become more advanced than ever, enterprises were rapidly shifting the way they consume technology. The rise of cloud and mobile put sensitive assets outside of an enterprise’s perimeter and beyond the protection of legacy security vendors. SMBs were particularly at risk, as they were adopting the cloud more rapidly than big companies and historically did not have the resources to invest in security.
A handful of investment themes arose to solve these challenges:
June 5th: The AI Audit in NYC
Join us next week in NYC to engage with top executive leaders, delving into strategies for auditing AI models to ensure fairness, optimal performance, and ethical compliance across diverse organizations. Secure your attendance for this exclusive invite-only event.
- Back to the (better) basics: Improve the usability, effectiveness, and cost of fundamental security technologies, such as identity and access management, endpoint protection, and application security. This is all the more important for protecting SMBs.
- Analyze and automate: Leverage big data, visualizations, AI, and automation to better assess risk, identify breaches sooner, and respond to incidents faster.
- Solve the people problem: Save employees from themselves with better security training and security products that don’t impede productivity. Leverage white hat and third-party services to supplement understaffed internal teams. Confuse advanced attackers with deception technology.
- Fortify the new fronts: Deploy a new generation of technology to secure the cloud, mobile, containers, and IOT (including connected cars and drones).
- Rise of DevSecOps: Empower security teams to keep pace with the rapid deployment cycles in the world of continuous integration and continuous deployment (CICD).
From 2014 to 2016, the nonstop beating of the data breach drum continued to reinforce the need for new security technology. Breaches included Home Depot, JPMorgan, Sony Pictures, Anthem, Yahoo, and the United States Office of Personnel Management, to name just a few incidents.
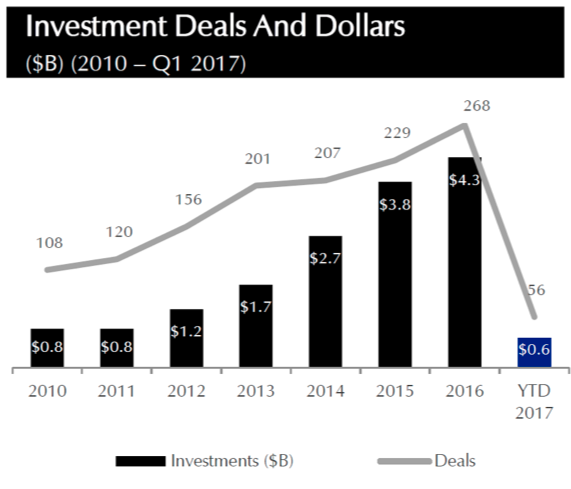
Above: Venture investment in cybersecurity since 2010.
Some will say cyber reached a peak in 2016. That year, RSA was just a madhouse of new companies and buzzword bingo. It seemed like five companies were all attacking the same problem and it’d become hard for customers, industry analysts, and investors to tell the difference. It’s also evident that cybersecurity has too much investment activity when you see more and more chief information security officers (CISOs) proactively seeking out roles at startups.
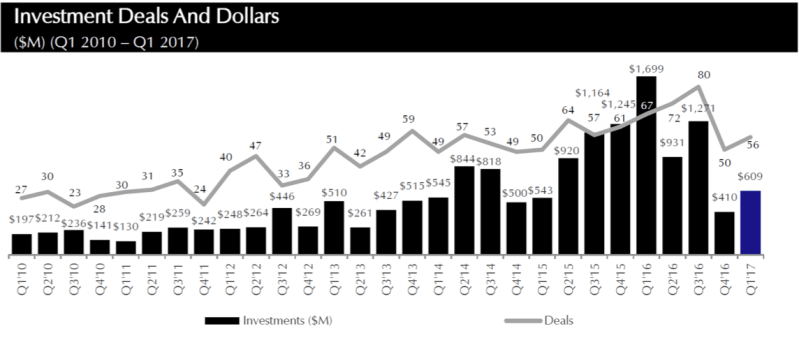
Above: Cybersecurity investment by quarter 2010-2017.
Throughout the last year, investor appetite in security continued to soften, generally aligning with the technology industry more broadly. Public tech stocks took a hit in early 2016 and private investors increasingly started to realize that round sizes and valuations for startups were high relative to exit potential. Furthermore, while customers were adopting next-gen security technology, it was not happening as rapidly as everyone had anticipated. Revenue, cash burn, and valuations were just too far out of line, and in 2016 we started to see the faltering of formerly high flying startups like Bromium.
The rest of 2017 will likely reveal more companies running into trouble. Yes, there will be some successful large exits, as there are with any cycle, but mega-rounds have slowed down. M&A should pick up as large vendors look to expand their product portfolio with new technology by picking up cash-strapped startups. Nevertheless, major security incidents so far this year demonstrate that fundamental problems remain to be solved. We are still early in the adoption cycle for next-gen security technology. Startups will continue to be funded, albeit at a slower pace and at lower valuations, as growth expectations align with reality.
Aaron Jacobson is a principal at NEA, a Silicon Valley venture capital firm.

