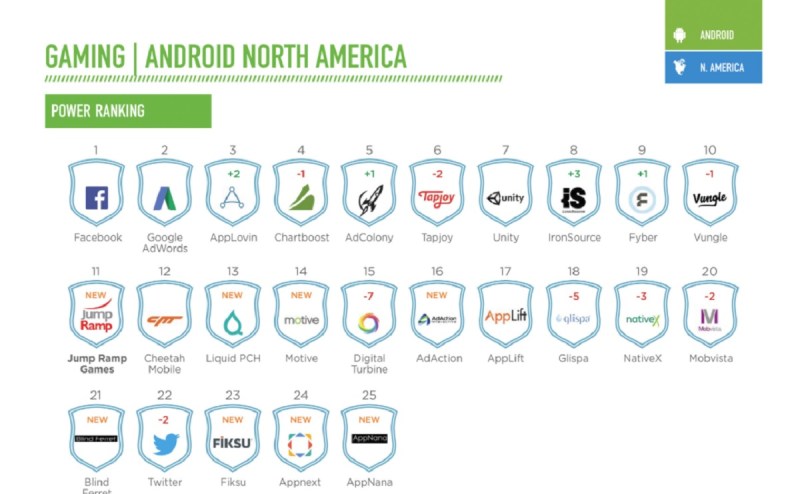
Above: JumpRamp Games is a user acquisition company based in New York.
GamesBeat: Another question is: Can we prevent cyberattacks, and if so, what are the steps to take?
Safarian: It’s a loaded question. I’m going to flat-out say no. You can’t prevent it. There’s always going to be a bad actor. If you have, for example, any end point, any API, you are available for an attack. There’s a liability there. There’s always going to be a bad actor out there that’s going to try to attack your system. You can’t prevent that, in my opinion.
All you can do is lessen your attack surface area. Use best practices. Build those robust guardrails around your most critical systems. If anybody is working on a cloud or a private VPN, you want to make sure you have your ports locked down, your security groups in line. At the most basic level, are there any mid servers you need to have on any of these nodes? What are the monitoring and detections like? Are any back doors exposed?
There are best practice white papers all over the place. Do yourself a favor. The business will always force you to develop and iterate quickly. It’s your responsibility, as a developer or a dev ops engineer, to pump the brakes a bit and fight back. “I understand we have this feature, this next thing we need to get out there, but we have a serious risk sitting here that can put a stop to everything we’re working so hard for.” Your voice needs to be important in those conversations. Again, you’re on the front lines. You’re going to bubble this information up for those critical strategic details that need to be acted on.
You can be proactive. If there’s a known phishing threat, for example, or a list that’s been exposed — user emails and passwords — how is that applicable to you? Nine out of 10 times, if there’s a user that’s been exposed before, they’re going to be compromised in your system as well. It’s simple things. People generally use the same password across the board. We’ve increased our IQ around that a little bit and people are being more aware, but there is a large chunk of the population across the globe that still does not adhere to any of those practices. As soon as a password is compromised in one area, a bad actor is going to take those exact credentials, run a script, and bombard your system. You need to figure out a way to deter that. How can you build a system, or rules, around helping your users get out of that rut?
There’s a bit of education you need to do as well. As a company we need to help educate our users and lead them. Whether it’s stronger password protection, whether it’s encrypting or hashing certain data — when you’re storing this data, make sure it’s not easily accessible.
Haghighi: Always, security is not 100 percent. Even if you try to protect everything as much as you can, there’s always a new way, a new technology, new areas that can leak. If you’re using an API, for example, you always have to have some concerns about that.
As far as prevention, you have to analyze your work flow first. You have to know your game architecture, your service architecture, and your organization architecture, all those working data flows. You have to come up with security plans around your work as much as you can. The hacker is trying to turn that around and find any way to come into your system.
According the last set of statistics and reports I got from our security company for 2017, attackers have even been trying to use apps they’ve published themselves on the Google Play store. Users download these apps, install them, and they act as zombies or weak links for attackers. Hackers can use these resources to attack a game through DDoS attacks, web traffic attacks, brute force attacks, and others. We have to build an educational plan, for employees and for users.
Part of prevention, in the beginning, is using monitoring tools. Don’t allow any weird attachments into your development team, your dev ops team, your customer service teams. Everyone should be trained about that. Never use free software. You have to think about why software and tools are free. Monitor abnormal traffic. You have to have defensive tools and a defensive strategy around things like firewalls and IPS. Meet regularly to think of any possible breaching areas and try to fix that with your developers and dev ops team.
According to reports, maybe 86 percent of attacks these days target the gaming industry. We have to think about many kinds of attacks, including DDoS attacks and web attacks. You need a solution for that. If you’re using the cloud, you have to come up with cloud mitigation solutions. If you run your own data center or co-location, you have to think about other kinds of mitigation services. Upgrade knowledge, use new technology, and do all the training you can.
Once your employees and staff are trained, that can keep hacking activity from even coming to your network. Everyone knows about social hacking and social engineering. That can come to your organization without any activity on your network. You have to think about training and talk with your employees and users about what not to trust. There are many ways you can find malware emails and the like. You have to do training with your employees.

Above: Even Steam falls victim to fraud from cyber criminals.
GamesBeat: I see frequent news about cyberattacks of all kinds. We all saw the non-game industry attacks that happened during the U.S. presidential election. That’s raised awareness among people around the world that this is a serious problem that hasn’t been solved. Every now and then you see something more catastrophic. A serious case last year involved Valve’s Steam service, where 77,000 of its accounts were being hacked every month, and it uncovered this script-kiddie malware, SteamStealer, that made it easy to prey upon people with lousy passwords.
Haghighi: I have a few statistics. According to reports I’m getting, in the second and third quarter of 2017, DDoS attacks in the gaming industry increased four percent. 86 percent of DDoS attacks are happening in the gaming industry. Several other industries — telecom, finance, software, education, retail, media, entertainment — all that together is less than five percent. The UDP fragment attack is the most popular, still, but hackers are also using DNS, NTP, and other vectors of attack. A company should make preparations against these kinds of attacks.
For DDoS attacks, they fall into two different categories: infrastructure attacks and application layer attacks. For applications, attackers are using GET, PUT, and POST vectors that you have to make sure of. Regarding web application attacks, in the third quarter of this year, we’re still seeing SQLi attacks and LFi attacks on the top. Any developer or publisher has to be careful of these kinds of injection attacks and others.
Depending on the region you’re in, and other criteria, different kinds of attacks are going to happen. You have to come prepared with different kinds of solutions. It’s very normal, in the gaming industry — for example, we’re closing in on Christmas this year. Depending on the game and the area you’ve launched that game, you have to expect some kind of attacks, but you can prepare for specific ones.
Safarian: The fact of the matter is, as a business, you’re working hard to create a positive user experience, some kind of value-add, some kind of evergreen application. We’re all fighting for that prime real estate, as application developers or game developers. We’re fighting for that place in the user’s daily regimen. The average user is going to maybe engage with four, five, six applications. We’re all fighting for that real estate.
Now imagine that you’ve worked so hard to become one of those evergreen applications and now everything just falls apart, because of those bad actors that we keep talking about here. The IQ and the attack preparation around these hits, they’re only increasing. Every week there’s new tech and more vulnerabilities being exposed. At some points these vulnerabilities are coming a lot faster than the solutions, the stability and the security. Yes, these things are the things that keep me awake at night, because again, you don’t know what you don’t know. A lot of new things are coming up every day that people are trying to use to destroy the stuff you’ve worked so hard for, to try to create this positive experience for your users.
People who say that they’re concerned, but not worried, I’m happy. I’m glad the anxiety hasn’t crippled them to the point where they’re awake at night. My question back to the would be, how critical are these things in your application or your game? If there are systems that are not super critical, that you don’t mind — what’s the cost-effectiveness of getting hacked? At some point you will have to evaluate that. “It’s not worth it for us to prevent an attack here.” That’s the ugly truth sometimes, speaking from a business standpoint.
Things are improving every single day on the security side of things. However, I just don’t feel like it’s as fast as the vulnerabilities that are being exposed.

Above: PlayStation Network got hit in 2011.
GamesBeat: When an attack happens, how do we deal with it and help avoid reputational damage? We’ve covered a lot of that already, but the reputational side of things is a new topic here.
Haghighi: It comes in two different parts. First, let’s say, once the attack happens, what are you going to do? It doesn’t necessarily matter what kind of attack in this case. If you google anywhere, you can find plenty of reasons to say, “Don’t panic.” Of course, you’ll get a lot of complaints once an attack happens — from your CEO, from your founders, from players, from the news media, everywhere. But first, you can’t panic or give in to stress. You need to be calm. You need to think about the scope of the attack, and stay calm.
In my previous experiences, in use case scenarios and live scenarios in this industry and other industries, at first you may know what happened. Users can’t log in, maybe, or your administrator password has changed, or your services are down, but you don’t know why. You should never try to turn off anything right away — servers, routers, service. You have to think about that. You have to start to investigate that first.
Definitely, you need initial plans. You have to come up with team management plans. You have to think about who can help you. You have to have a strategy coming from your IT department or security department, and then you have to go with the recommendations of that plan.
The first thing should be to measure the scope of impact. Let’s say, if the service is totally gone, you have to think about how you can turn it back on. You need initial backup plans for that — backup service, disaster plans — to be able to start the service running again. Then you can start tracing the activity in your network. Maybe the hack has left some logs, or your monitoring tools can help you with that part. You need to investigate as much as you can, find any logs you can, and find the leaking area.
You need to monitor inbound and outbound traffic, but that should be in a totally transparent mode. You have to think about that. If the hacker recognizes that you’re tracing them, they’ll stop activity. You have to be transparent, but you have to monitor to find out what they’re doing. Or if this is a DDoS attack — let’s say it’s saturated your bandwidth, saturated your service in total. You have to find a way to connect to your service again and relaunch it.
For all of this you have to have initial plans. You could reroute traffic, for example. Different companies have honey pot services, so you can route your traffic there and then start the rest of your plans. You can block malicious activities, start the server network cleanup, and restore data. It depends on the attack, but you may have to restore some data. Restoration should be a shared experience with a trusted party. In some cases you have to bring in a consulting company, a third party, to help you, if your team on your company’s side can’t help with the issue.
These are the technical parts that you have to deal with if an attack happens. Regarding reputation, of course, the first point is your users. They may be aware of an issue, but they don’t know what’s happening. You don’t need to share that you’re hacked, or that you have an issue, but you have to have a prepared web space, prepared services, so you can redirect traffic to a maintenance mode and then say, “This is the issue and we have to investigate.”
You have to make sure you have a good compensation plan and package. It depends on the service, but since we’re talking about games, we have some in-game services, in-game events. We have to have satisfaction plans and packages that we can come up with, so we can talk about that with users. It all depends on the scope of impact. If it’s only affecting a few users’ information, you can deal with them directly without any public announcement. If it’s the entire game, the entire service impacted, you have to come up with a plan to publish that news.
You can potentially consult with third parties, especially if it’s happened before to similar companies, or if it’s a part of a global phenomenon like ransomware issues. But you need to be calm, and then you can find a lot of ways to avoid damage to your reputation.

