testsetset
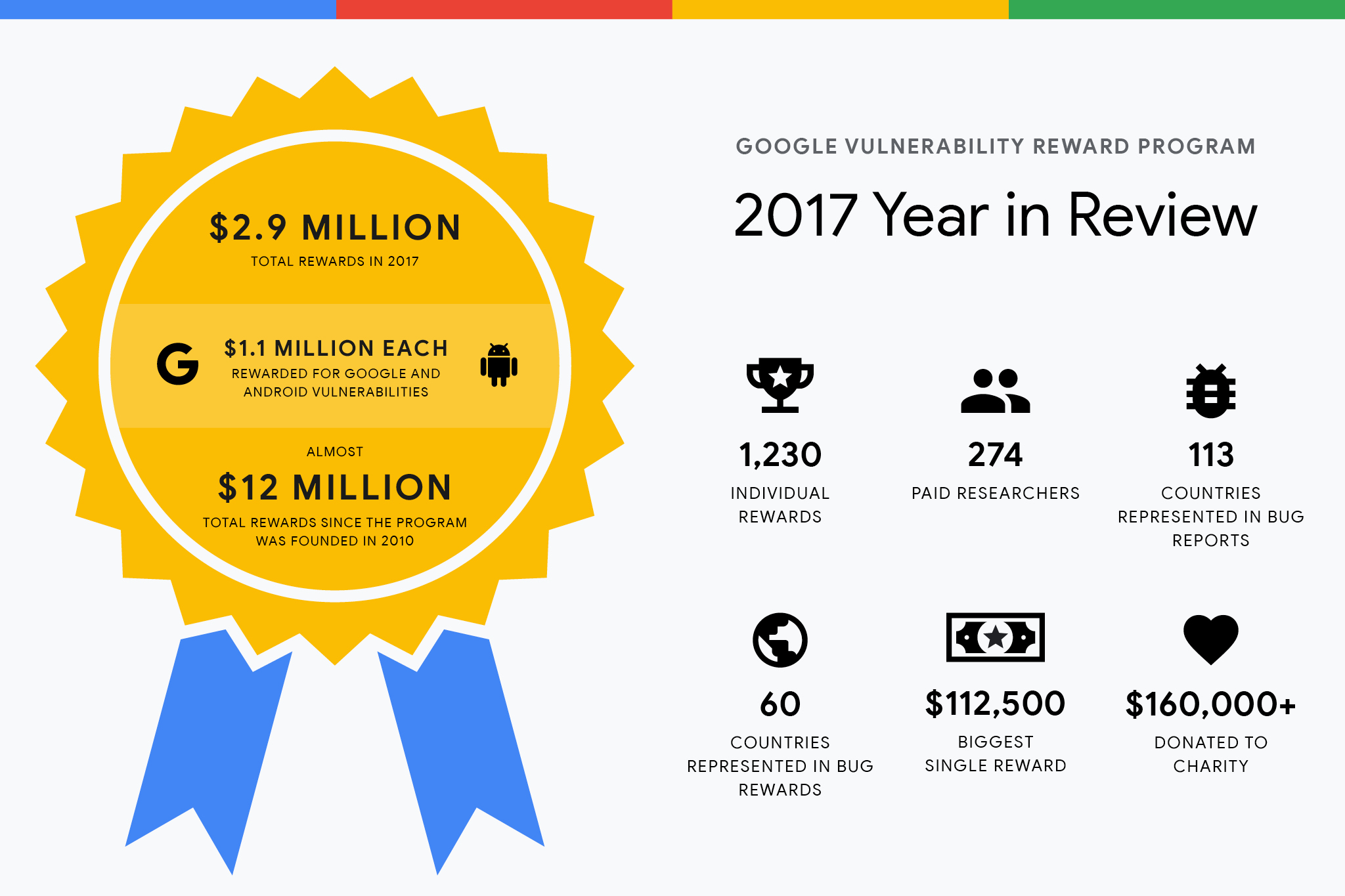
Google today announced it has paid out almost $12 million since launching its bug bounty program in November 2010. In the past year alone, the company paid 274 different security researchers $2.9 million, although the year before that it paid out over $3 million.
Bug bounty programs are an excellent addition to existing internal security programs. They help motivate individuals and groups of hackers not only to find flaws, but to disclose them properly when they do, instead of using them maliciously or selling them to parties that will. Rewarding security researchers with bounties costs peanuts compared to paying for a serious security snafu.
Google awarded researchers more than $1 million for vulnerabilities found and reported in Google products as well as in Android. Chrome rewards amounted to a little bit less, but still rounded out the remainder to get the total to $2.9 million.
June 5th: The AI Audit in NYC
Join us next week in NYC to engage with top executive leaders, delving into strategies for auditing AI models to ensure fairness, optimal performance, and ethical compliance across diverse organizations. Secure your attendance for this exclusive invite-only event.
Google said it awarded $125,000 to more than 50 security researchers. The company also doled out $50,000 to those who improve the security of open source software as part of its Patch Rewards Program.
Google also shared three stories about its bug bounty program in 2017:
- In August, researcher Guang Gong outlined an exploit chain on Pixel phones which combined a remote code execution bug in the sandboxed Chrome render process with a subsequent sandbox escape through Android’s libgralloc. He received the largest Android reward of the year: $112,500.
- Researcher gzobqq received the $100,000 pwnium award for a chain of bugs across five components that achieved remote code execution in Chrome OS guest mode.
- Alex Birsan discovered that anyone could have gained access to internal Google Issue Tracker data and was awarded $15,600 for his efforts.
Google’s bug bounty program has been growing since its inception, although the results from the past few years look like a plateau. Still, Google’s security team continues to expand the program to encompass more products and offer more lucrative rewards, such as up to $100,000 for hacking a Chromebook and up to $200,000 for hacking Android.
Indeed, Google today expanded its Google Play Security Rewards Program, which debuted in October. The company expanded the range of rewards for remote code executions from $1,000 to $5,000, and added a new $1,000 category to include vulnerabilities that could result in the theft of users’ private data, information being transferred unencrypted, or bugs that result in access to protected app components.

